
Virus Total (VT) is an online service that analyses files and URLs for malicious code (such as viruses, worms, trojans etc) using antivirus engines.
Many enterprise security products leverage VT and its extensive database of malicious file information by uploading unidentified files for analysis.
Mossé Security has been observing that some security solutions automatically upload emails to VT that contain sensitive information (including attachments), without the knowledge or consent of the organisation.
Organisations worldwide are urgently advised to immediately:
In this urgent security advisory, we present files pertaining to Australian organisations but Mossé Security CSIRT confirms that organisations worldwide are affected by this.
The amount of sensitive information found on VT is staggering. Leaked documents include but are not limited to the following.
Legal Documents for In-Development/Progress Legal Cases
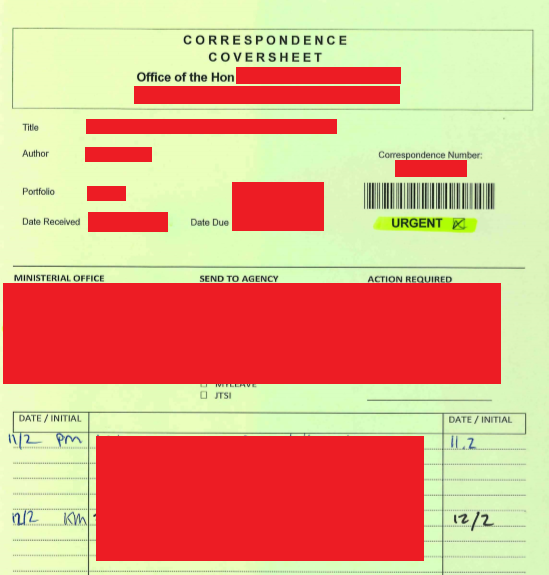
We identified various documents and communication fragments pertaining to a legal case involving two large infrastructure organisations:
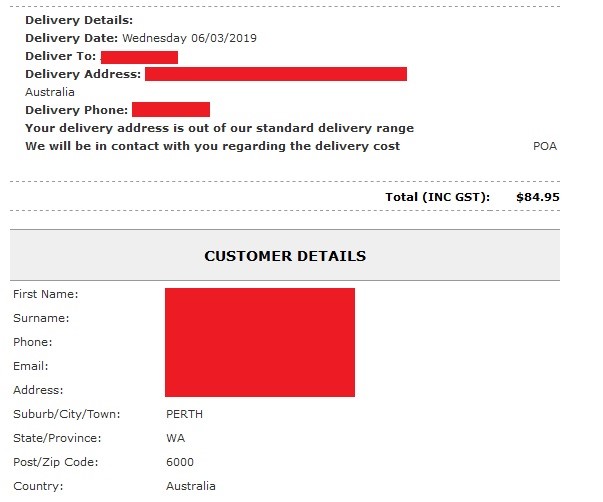
Profiles, police ticket receipts, sales invoices and property valuations:

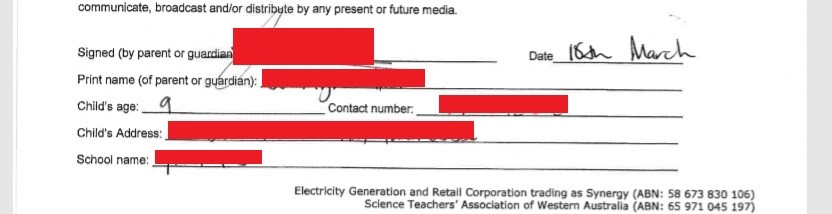
One very concerning pieces of data uncovered in our findings were children’s release/permission forms, including their name, age, address, their school and phone number.
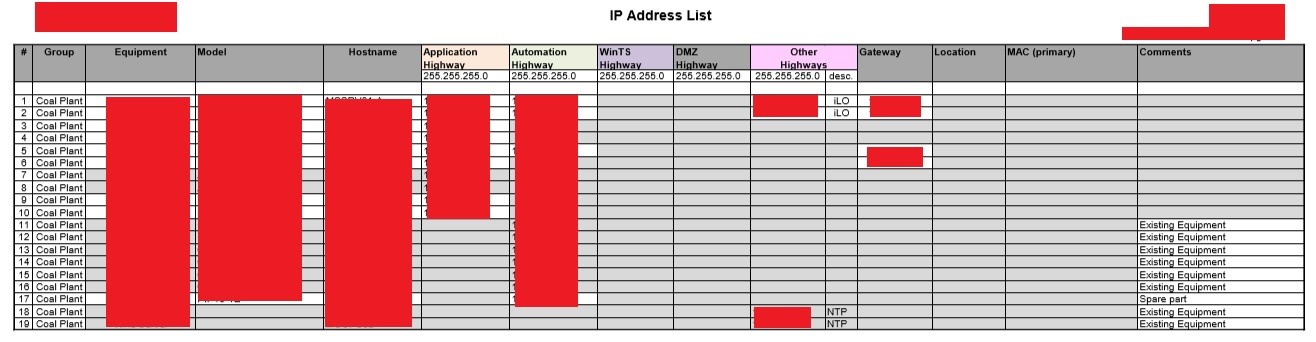
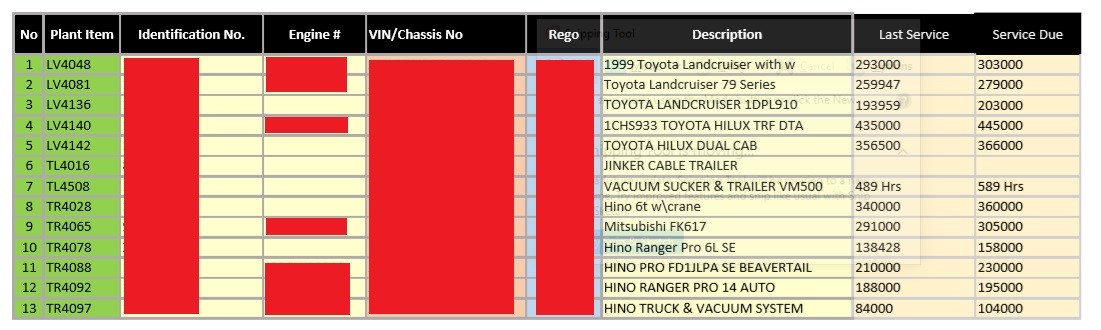
Our investigation uncovered leaked infrastructure (including Powerplants) documents, detailing IP addresses, firewall rules, maintenance records, as well as operational data.
Many of the emails recovered included copies of staff ID card, driver’s licenses and certificates as attachments.

A large portion of documents recovered pertain to business activity including contract and business bids, as well as large purchase invoices.
Company Logistics Details: Fleet Information, Staff Competencies
Documents containing technical details of company assets, staff competencies, certificates and training levels.
To ensure your organisation is safeguarded against data leakage stemming from Virus Total uploads, we recommend the following:
Published: 16/07/2019