
UPX is an executable file compressor. In this blogpost, we share a simple anti-virus (AV) evasion technique based on UPX that works well against AI-based anti-virus software.
UPX is legitimately used to reduce the file size of Portable Executables by around 50%-70%. It is also often used by threat actors to add a layer of obfuscation to their malware. The default version has a "decompress" flag which will retrieve the original code. The technique presented in this blogpost will prevent this feature from working, forcing anti-virus software to use custom unpacking solutions.
The technique involves packing an executable with UPX and then modifying one byte.
We decided to use Mimikatz as a test case as it's a leading post-exploitation tool commonly used by penetration testers, Red Teamers and real threat actors.
We start with packing the Mimikatz executable with UPX:
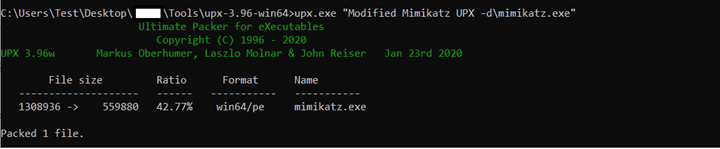
We then edit the executable with a hexadecimal editor:
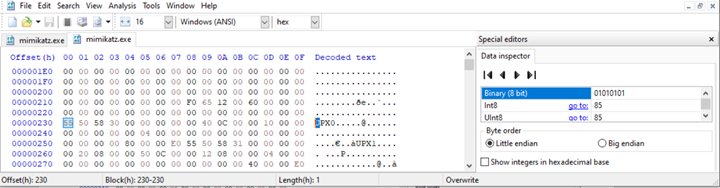
As you can see there is a string “UPX0”. We alter this by one byte to result in “BPX0” which renders the .exe to fail when trying to unpack as shown in the screenshot below. The executable will continue to work fine though.
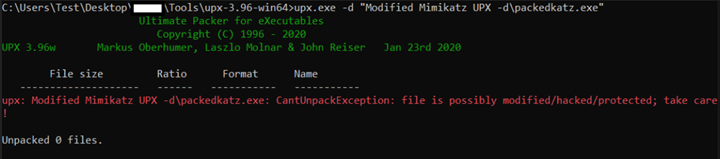
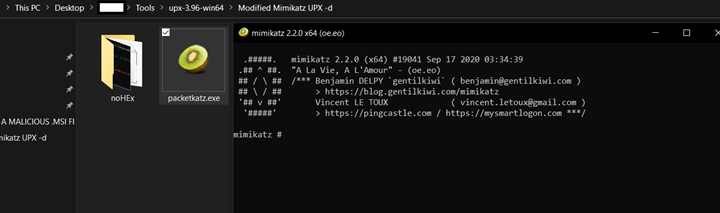
The screenshot shows that Mimikatz continues to work as it should:
As of writing this blogpost the detection rate on Virus Total for a vanilla “Mimikatz.exe” was 45 engines:
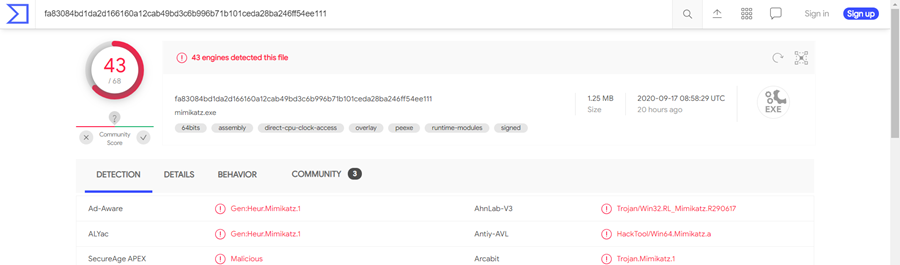 Modified Mimikatz:
Modified Mimikatz:
In comparison, the version of Mimikatz packed with UPX and then manually edited was only detected by 29 anti-virus software:
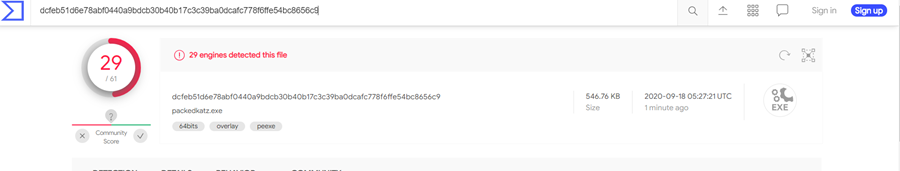
Never upload your custom Red Team tools to Virus Total. The files will be downloaded by all the anti-virus companies and kept in perpetuity for retro-hunting purposes.
References:We initially stumbled across this technique on stackoverflow.
29/09/2020